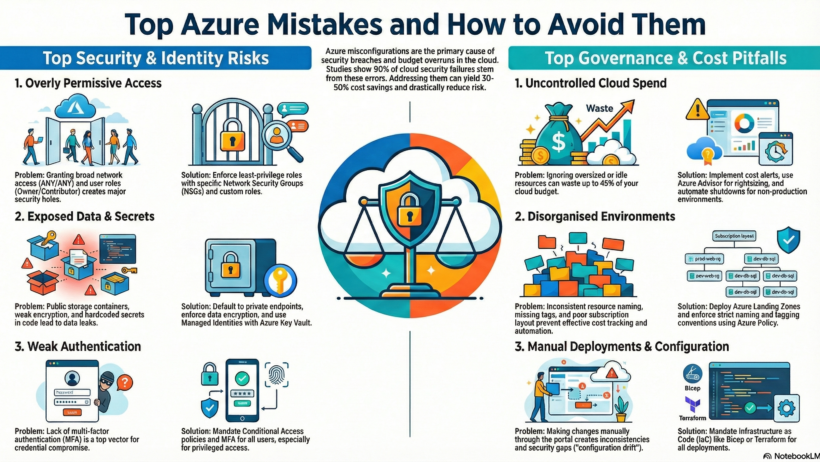
As Microsoft Azure continues to dominate the cloud landscape in 2026—with global cloud spending surpassing $1 trillion—Azure misconfigurations remain the leading cause of security breaches, cost overruns, and operational disruptions. Studies show that 90% of cloud security failures stem from misconfigurations, often costing organizations millions in breaches and wasted spend.
This comprehensive guide highlights the 15 most common Azure mistakes and misconfigurations in 2026, drawn from the Azure Well-Architected Framework (WAF), Microsoft Defender for Cloud insights, industry reports, and real-world audits. Tailored for:
- DevOps Engineers: Focus on automation, IaC, and pipeline security
- Cloud Architects: Alignment with WAF pillars for reliable, scalable designs
- Business Leaders: Understanding financial risks, compliance impacts, and ROI optimization
Avoiding these Azure pitfalls can deliver 30-50% cost savings, drastically reduce breach risks, and accelerate innovation.
1. Poor Subscription Organization and Landing Zone Neglect
The Problem: Using a single subscription with scattered resources, ignoring Azure Landing Zones.
Risks and Considerations: Leads to governance failures, shadow IT, compliance violations (e.g., GDPR), and uncontrolled costs. Architects face challenges with policy inheritance; businesses risk audits and fragmented billing.
The Fix: Deploy Azure Landing Zones with management groups and separate subscriptions per environment/workload. Use the Azure Landing Zone Accelerator for automated setup aligned with WAF.
2. Inconsistent Naming Conventions and Missing Tagging
The Problem: Arbitrary resource names and no mandatory tags.
Risks and Considerations: Impedes automation, FinOps reporting, and cost allocation—executives lose departmental spend visibility; DevOps pipelines fail on inconsistencies.
The Fix: Enforce standards via Azure Policy and Naming Tool. Require tags for cost center, environment, owner, and app.
3. Lack of Automated Azure Policy Enforcement
The Problem: Manual guidelines without policy-as-code.
Risks and Considerations: Configuration drift undermines WAF reliability/security, increasing technical debt and remediation expenses.
The Fix: Use deny/audit policies integrated with IaC pipelines (Bicep/Terraform).
4. Overly Permissive Network Security Groups (NSGs)
The Problem: ANY/ANY rules or open ports (e.g., RDP/SSH from internet).
Risks and Considerations: Primary attack vector in 2026 breaches; breaches zero-trust and exposes to ransomware.
The Fix: Default-deny NSGs, least-privilege rules, Azure Firewall, and DevOps approvals.
5. Publicly Exposed Storage Accounts or Blobs
The Problem: Anonymous access on containers.
Risks and Considerations: Frequent data leaks; massive GDPR/HIPAA fines and reputational harm.
The Fix: Private endpoints default, temporary SAS tokens, and Defender for Storage.
6. Relying on Secrets Instead of Managed Identities
The Problem: Hardcoded keys/secrets in code/configs.
Risks and Considerations: Leak risks in repos/pipelines; slows DevOps with manual rotations.
The Fix: Use managed identities + Key Vault; enforce in IaC.
7. No MFA or Conditional Access Enforcement
The Problem: Legacy auth or no MFA on Entra ID.
Risks and Considerations: Top credential compromise vector; regulatory non-compliance.
The Fix: Mandatory Conditional Access blocking legacy auth; PIM for elevated access.
8. Overprivileged RBAC Assignments
The Problem: Broad Owner/Contributor roles.
Risks and Considerations: Enables escalation/lateral movement; one compromise threatens subscriptions.
The Fix: Custom least-privilege roles, PIM for JIT, regular reviews.
9. Disabled or Weak Encryption
The Problem: No encryption at rest/transit or weak TLS.
Risks and Considerations: Compliance failures (PCI/HIPAA); data interception.
The Fix: Azure Disk Encryption, CMKs, enforce TLS 1.3 via policy.
10. No Cost Monitoring, Budgets, or Alerts
The Problem: No budgets or anomaly detection.
Risks and Considerations: Bill shocks from idle resources—up to 45% waste; erodes ROI.
The Fix: Azure Budgets with alerts, Cost Management, Advisor automation.
11. Overprovisioning and Skipping Rightsizing
The Problem: Oversized VMs/databases running idle.
Risks and Considerations: Unnecessary waste; missed Reservations/Savings Plans.
The Fix: Advisor recommendations, auto-scaling/shutdowns, Reservations for predictable loads.
12. Inadequate Backup and Disaster Recovery
The Problem: Relying on redundancy without tested backups.
Risks and Considerations: Data loss from ransomware; impacts continuity.
The Fix: Azure Backup with immutable vaults, Site Recovery, regular tests.
13. Manual Deployments Instead of IaC
The Problem: Portal changes over Bicep/Terraform.
Risks and Considerations: Drift, inconsistencies slow DevOps.
The Fix: Mandate IaC with policy scans (e.g., Checkov).
14. Insufficient Monitoring and Logging
The Problem: Incomplete Azure Monitor/Defender setup.
Risks and Considerations: Blind spots delay response; compliance gaps.
The Fix: Centralized Log Analytics, full Defender enablement, observability in designs.
15. Ignoring Azure Advisor and WAF Reviews
The Problem: Overlooking Advisor or periodic assessments.
Risks and Considerations: Accumulating debt across pillars; missed optimizations.
The Fix: Quarterly WAF Reviews, automate Advisor remediations, tie to governance.
Conclusion: Secure Your Azure Environment in 2026
These common Azure misconfigurations and mistakes drive most cloud incidents—but they’re preventable. Align with the Azure Well-Architected Framework for resilient designs. DevOps teams achieve safer deployments; architects build scalable systems; leaders gain predictable costs and reduced risk.
Start with an Azure Well-Architected Review and enable Microsoft Defender for Cloud. Turn these pitfalls into advantages—your competitive edge in 2026.
What Azure mistakes have you seen? Share below!